Who remembers the nice & quiet start to December of 2021, everyone shifting their focus to holiday planning - both gift buying and on-call scheduling, when a little gem eternalized as log4shell gets announced, and havoc ensues?
If you worked on a Java project, or at a company that even has a Java project, the name log4shell may bring back a headache or two.
log4Shell1 was a trifecta of several borderline programming practices, all joining force to be what may have been the biggest ever security vulnerability.
I think that the worst thing about log4Shell was how easy it was to take advantage of. Hackers were writing out messages everyone on the internet, and the vulnerable servers would literally call out to the hackers to identify itself by a ping-back or DNS lookup.
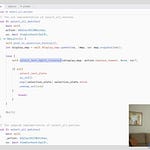
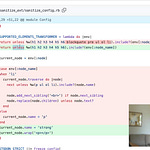
Disclosed on December 10th publicly, 2 commits2 were already in place by December 4th - 6 days prior to the public announcement. Both commits addressed the issue but didn’t completely fix the followup CVEs - until a December 12th commit3 finally squashed the issue - also squashing some of the interesting functionality that log4j offered that led to the issue in the first place.
In this episode, we relearn a bit about what log4Shell was, and we examine the 3 commits that fixed it.